
Why wouldn’t you add another security layer to your MS 365?
Managed Network Services, Security
2FA Is a Simplified User Experience
Two-factor authentication gives you that second layer of security beyond a password while still making it easier on the user, than MFA.
2FA Protects Against Unauthorized Access
With the introduction of…

Week in Breach
Security
Hi Brett,
Here is breach news to share with your customers!
This week, data breaches threaten future government contracts, PII is exposed online, and cybersecurity incidents are projected to reach…

Sales Management Training
Innovative Ideas, ProductivityBTA Sales Management Leadership Participant Quotes
“Highly comprehensive program with resources and skills that will impact personal and team improvement. Excellent content and well presented.”
Hunter McCarty – COO
RJ Young
Nashville,…

How to hack a printer. Diary of a bored hacker.
Security
Printers gone mad
December 5, 2018
One quiet evening, you suddenly hear a sound. It’s the printer in the next room, and it’s furiously printing something no one requested. You take a look and see that it’s printed a leaflet…
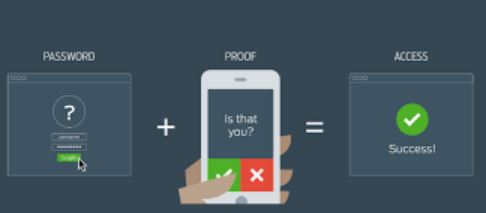
We just deployed multi-factor authentication at another Managed Services Client
Managed Network Services, SecuritySEPTEMBER 23RD, 2019
Quickly and Easily Secure Local Microsoft Windows Logins
Administrators and users often have a lot of sensitive information stored in their Windows laptops and desktops or local machines. Even with the availability of cloud…
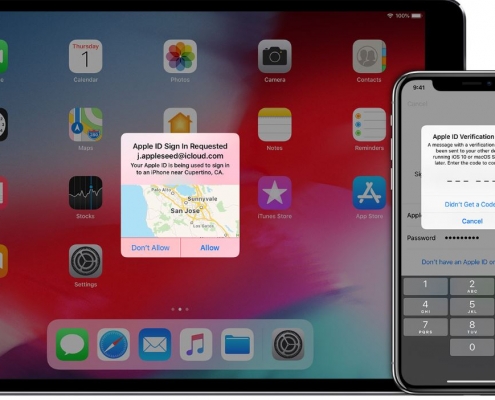
Two-factor authentication for Apple ID
Security
How it works
With two-factor authentication, your account can only be accessed on devices you trust, like your iPhone, iPad, Apple Watch, or Mac. When you want to sign in to a new device for the first time, you'll need…

5 Ways AI Is Transforming The Customer Experience
Business Intelligence, Innovative Ideas, Productivity
Daniel NewmanContributor
CMO Network
GETTY
We all know that artificial intelligence is playing a huge role in how businesses operate. AI programs and services are helping transform everything from data collection…

Week in Breach
Security
This week, phishing scams continue to trap employees, weak passwords put company data at risk, and the consequences of a breach are higher for SMBs.
Dark Web ID Trends:
Top Source Hits: ID Theft Forums
Top…

5G Is Coming Soon. Do You Care? You Should. Here’s Why.
Business Intelligence, Innovative Ideas, Productivity
Upgrading U.S. wireless networks has been called our most important infrastructure project. It’s actually happening.
National Geographic
PUBLISHED JANUARY 23, 2018
PROGRESS…

Why Organizations Want Consumption-Based Artificial Intelligence Pricing
Business Intelligence, Innovative Ideas, Productivity
ARTIFICIAL INTELLIGENCE AND DAAS
Sep 11,2019 / By Ritu Jyoti / No Comment
Artificial intelligence (AI) adoption is at a tipping point, as more and more organizations develop their AI strategies for implementing the revolutionary…
