Tag Archive for: Cyber crime

Week in Breach
Security
Hi Brett,
Here is breach news to share with your customers!
This week, data breaches threaten future government contracts, PII is exposed online, and cybersecurity incidents are projected to reach…

How to hack a printer. Diary of a bored hacker.
Security
Printers gone mad
December 5, 2018
One quiet evening, you suddenly hear a sound. It’s the printer in the next room, and it’s furiously printing something no one requested. You take a look and see that it’s printed a leaflet…
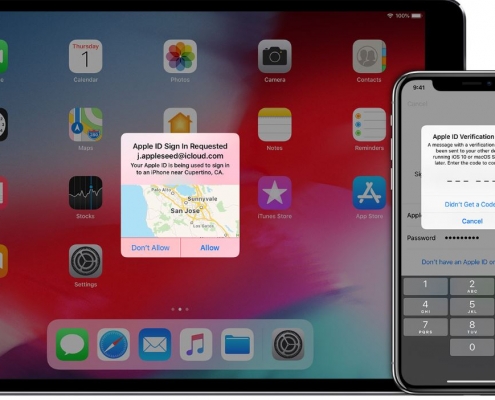
Two-factor authentication for Apple ID
Security
How it works
With two-factor authentication, your account can only be accessed on devices you trust, like your iPhone, iPad, Apple Watch, or Mac. When you want to sign in to a new device for the first time, you'll need…

Week In Breach
Managed Network Services, Security
This week, customer loyalty programs are compromised, employees continue to fall for phishing scams, and data breach costs continue to increase.
Dark Web ID Trends:
Top Source Hits: ID Theft Forums
Top Compromise…

35 Interesting Facts about The Deep Web
SecurityThe deep web is usually described as a dark, secretive and dangerous place. But just what exactly is it and what is the truth behind it? should it be banned? Find more on these Deep Web facts.
1. The Deep Web is “Web Content” that’s hidden.
2.…

One issue is probably to blame for your IT outages and data losses – and it’s not hackers
Managed Network Services, Security
The main causes of downtime remain prosaic, but cyber incidents are growing too.
By Steve Ranger | July 11, 2019 -- 14:38 GMT (07:38 PDT) | Topic: Security A hardware failure is most likely to cause unexpected downtime…

The Week in Breach
SecurityBreach news to share with your customers!
This week, databases are leakier than an old car on a bumpy road. Plus, Nest security may not be so secure.
Dark Web ID Trends:
Top Source Hits: Social Media (57%)
Top Compromise Type: Email
Top…

Network Security: What is Attack Surface Analysis and Why is it Important?
Managed Network Services, Security11/16/2017
1What is Attack Surface Analysis and Why is it Important?
2Defining the Attack Surface of an Application
3Identifying and Mapping the Attack Surface
4Measuring and Assessing the Attack Surface
5Managing the…

3 Email security trends MSPs shouldn’t ignore
Security
Posted by Brian Babineau on Jun 19, 2018 9:30:00 AM
Email security is a primary threat vector for businesses of all sizes, and that won’t be changing anytime soon. The nature of those email-borne threats is evolving, though,…

Why developing an internal cybersecurity culture is essential for organizations
Managed Network Services, Security
Help Net Security February 7, 2018
[Free CISSP Exam Study Guide] Get expert advice that will help you pass the CISSP exam: sample questions, summaries of all 8 CISSP domains and more!
ENISA published a report providing…
