Understanding Social Engineering
In today’s digital age, cybersecurity threats are more prevalent than ever before. Among the various tactics employed by cybercriminals, social engineering stands out for its cunning manipulation of human psychology, rather than relying on technical hacking skills. This guide aims to demystify social engineering, shed light on its workings, and offer strategies for Excel Office Services to shield itself against these insidious attacks.
What is Social Engineering?
At its essence, social engineering is a method of manipulation that exploits human error to gain private information, access, or valuables. Unlike typical cyberattacks that directly target systems, social engineering attacks the weakest link in the security chain: people. By appealing to basic human instincts, such as trust, fear, or the desire to help, attackers trick individuals into voluntarily handing over sensitive information or performing actions that compromise security.
How Social Engineering Works
Social engineering attacks often begin with the attacker researching and identifying potential victims. They might pose as a trusted figure—a bank employee, a company executive, or a customer support agent—to create a scenario that seems legitimate. Through crafted communication, usually via email, phone calls, or social media, they weave convincing narratives that prompt the victim to disclose confidential data, click on malicious links, or even transfer funds.
The Dangers of Social Engineering
The true peril of social engineering lies in its simplicity and effectiveness. A single deceived employee can unwittingly open the gates to widespread organizational harm. Modern social engineering schemes are sophisticated enough to bypass traditional defenses, making them a preferred method for initiating more severe cyberattacks, such as ransomware or advanced persistent threats.
Protecting Against Social Engineering
The key to defending against social engineering is awareness and education. Excel Office Services can adopt several proactive measures to cultivate a culture of security among its employees:
- Regular Training: Conduct interactive training sessions that simulate social engineering scenarios, teaching employees to recognize and respond appropriately to suspicious requests.
- Clear Policies: Implement and communicate clear security policies, including password management protocols and guidelines for handling unsolicited requests for information.
- Multi-Factor Authentication: Enforce multi-factor authentication for accessing sensitive systems and data, adding an extra layer of security beyond passwords.
- Email Security: Deploy advanced email security solutions with anti-phishing capabilities to detect and block fraudulent emails before they reach the inbox.
Common Types of Social Engineering Attacks
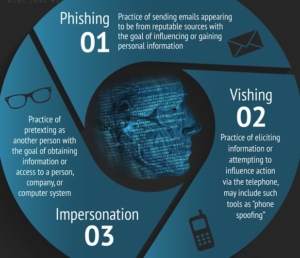
- Phishing: These attacks use deceptive emails to trick users into giving away personal information or downloading malware.
- Watering Hole: Cybercriminals compromise a frequently visited site to target a specific group, hoping to infect their devices.
- Business Email Compromise (BEC): Attackers impersonate company executives in emails, directing employees to transfer funds or share sensitive data.
- USB Baiting: Malware-laden USB drives are left in strategic locations, banking on the curiosity or goodwill of finders to plug them into a network.
As social engineering continues to evolve, so too must our strategies for combating it. For Excel Office Services, the path to enhanced cybersecurity begins with understanding the nature of these threats and investing in comprehensive employee education. By fostering a vigilant and informed workforce, we can fortify our defenses against the manipulative tactics of cybercriminals and protect our and yours invaluable data and resources.
Lets talk hunter@excelofficeservices.com